One of the most difficult problems in managing a large network is the complexity of security administration. The deployment of individual security products such as firewalls, intrusion detection systems, network traffic analysis, log file analysis, or antivirus software is never going to provide adequate protection for computers that are connected to the internet. For example, a good network intrusion prevention and detection system (such as Snort) does an exemplary job at detecting attacks within traffic. However, this type of detection does not offer any sort of damage containment. Equally, a firewall offers an outstanding method at defining what type of traffic is allowed in a network, but does not offer any deep protocol analysis.
A more coordinated approach is needed to ensure that an organisation retains data integrity and security. A popular approach is to deploy the ‘onion’ technique whereby multiple, overlapping layers of security are used to protect a network or computer. Using this technique, a system or network will have much more resilience from attacks.
One of the essential tools in hardening a computer system or network is to use access controls such as Mandatory Access Control (MAC) or Role-Based Access Control (RBAC). These controls include authentication, authorisation and audit. When a system mechanism controls some sort of operation on an object or target and an individual user is unable to alter that access, that control is defined as a mandatory access control. Whenever a user tries to access an object, an authorisation rule, defined by the system administrator, decides whether the access is permitted. This offers a powerful tool in damage containment to a system or network, and is frequently used where priority is placed on confidentiality.
Role-Based Access Control (RBAC) is an approach of controlling access to computer resources where the access policy is determined by the system, not the owner. It also ensures that only authorised users are able to perform authorised activities. The fine-grained security defines who or what process can use a system resource, as well as the type of access. Consequently, access permissions are administratively associated with roles, and users are administratively made members of appropriate roles. It is a modern alternative to Mandatory Access Control.
A properly-administered RBAC system enables administrators and end-users to carry out a range of authorised operations, yet at the same time retaining flexibility. It offers a powerful mechanism to reduce the cost, complexity, and risk of assigning the wrong permissions to users. System administrators can also control access at a level of abstraction that is natural to the way that enterprises typically conduct business, and make a significant difference in the simplification of the development and maintenance of provisioning processes.
To provide an insight into the open source software that is available, we have compiled a list of 5 capable MAC/RBAC tools. Hopefully, there will be something of interest here for anyone who wants a multi-layered detection, prevention, and containment model.
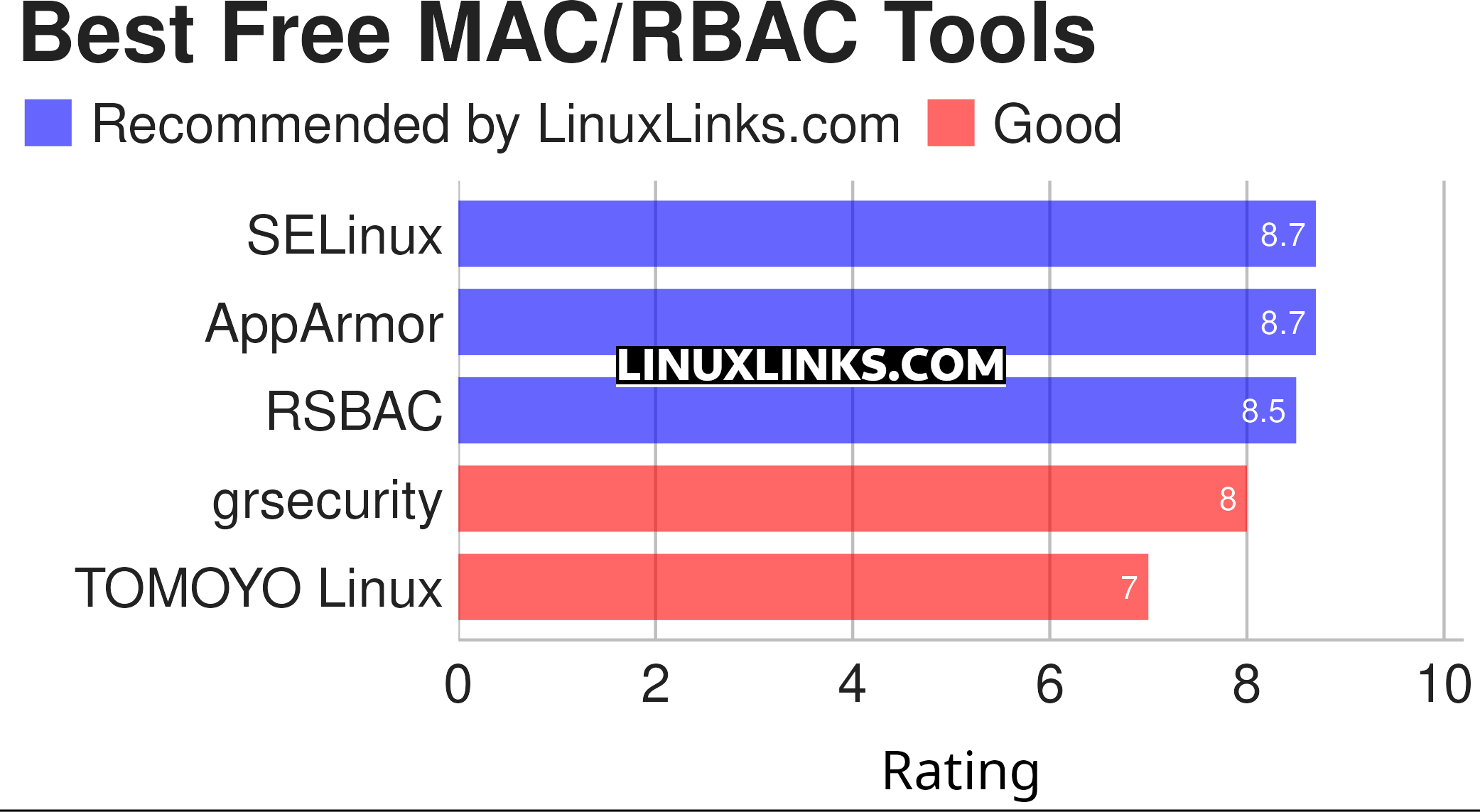
Let’s explore the 5 MAC/RBAC tools at hand. For each tool we have compiled its own portal page, a full description with an in-depth analysis of its features, screenshots, together with links to relevant resources.
| MAC/RBAC Tools | |
|---|---|
| SELinux | Security enhancement to Linux |
| AppArmor | Linux Security Module implementation of name-based access controls |
| RSBAC | Patch adding several mandatory access models to the Linux kernel |
| grsecurity | Innovative set of patches for the Linux kernel |
| TOMOYO Linux | Lightweight and easy-use Mandatory Access Control |
This article has been revamped in line with our recent announcement.
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |
Only grsecurity, which violates the GPLv2 since 2014, is RBAC. All other are MAC only. So there is no acceptable RBAC system in this article!