SSH or Secure Shell is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH.
SSH was designed as a replacement for Telnet and for unsecured remote shell protocols such as the Berkeley rsh and the related rlogin and rexec protocols. Those protocols send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis. The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
There are many ways to make a server running SSH more secure. Here are some examples: Disable root logins, use private key authentications (rather than ssh passwords), enable two-factor authentication, change the port used by SSH, don’t listen on every interface, limit users’ SSH access, and make sure the operating system is kept up-to-date.
There are more steps you can take to harden the server. This article recommends open source software that employ different techniques to make it harder for a server running SSH to be compromised.
We list our recommendations below captured in a legendary LinuxLinks-style ratings chart. All of the software featured here is published under an open source license.
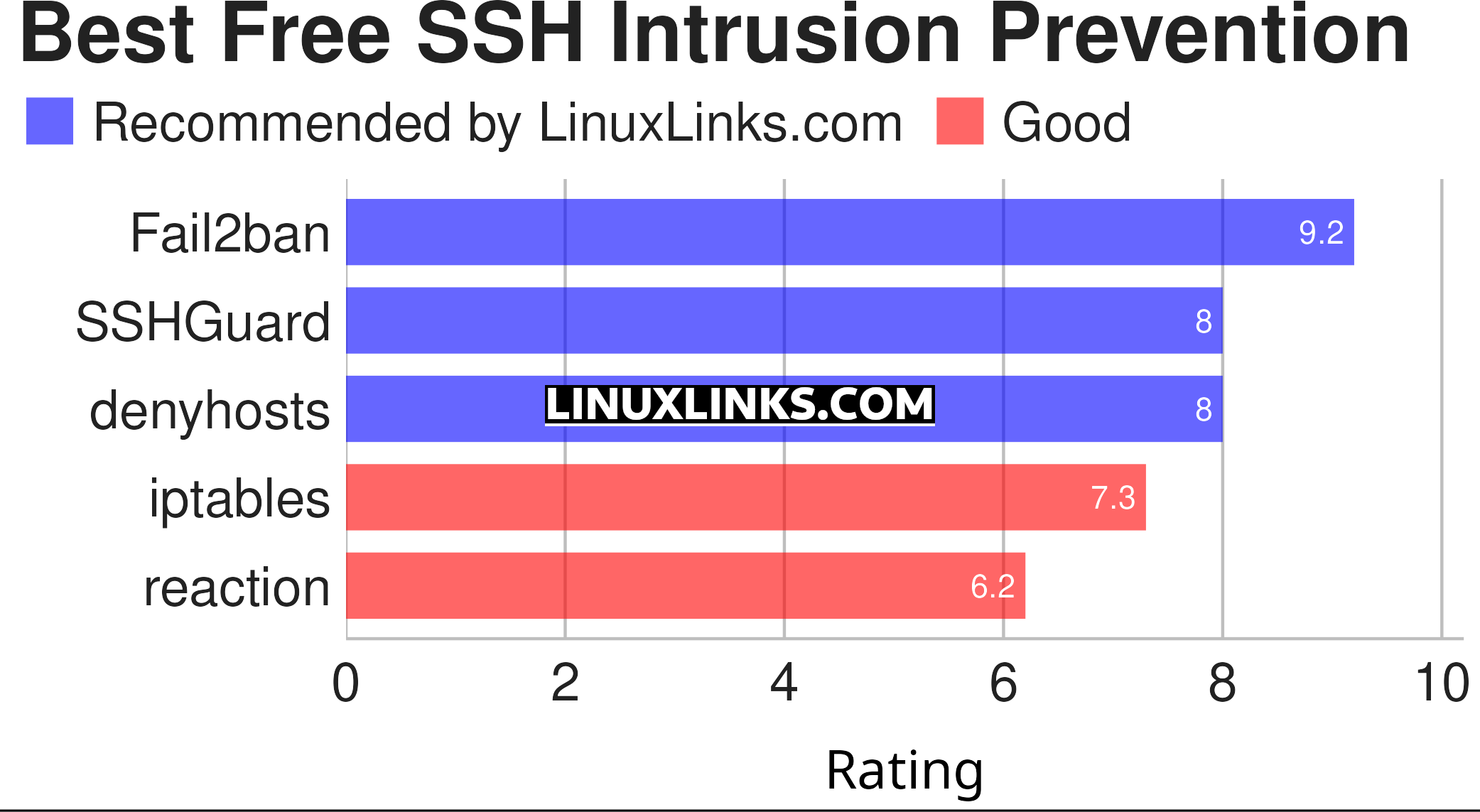
| Intrusion Prevention for SSH | |
|---|---|
| Fail2Ban | Intrusion prevention software framework written in Python |
| SSHGuard | Protects hosts from brute-force attacks against SSH and other services |
| denyhosts | Helps thwart SSH server attacks |
| iptables | Configure the Linux 2.4.x and later packet filtering ruleset |
| reaction | Daemon that scans program outputs for repeated patterns, and takes action |
This article has been revamped in line with our recent announcement.
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |
