An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations.
IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that detects malicious traffic on a network is an example of an NIDS.
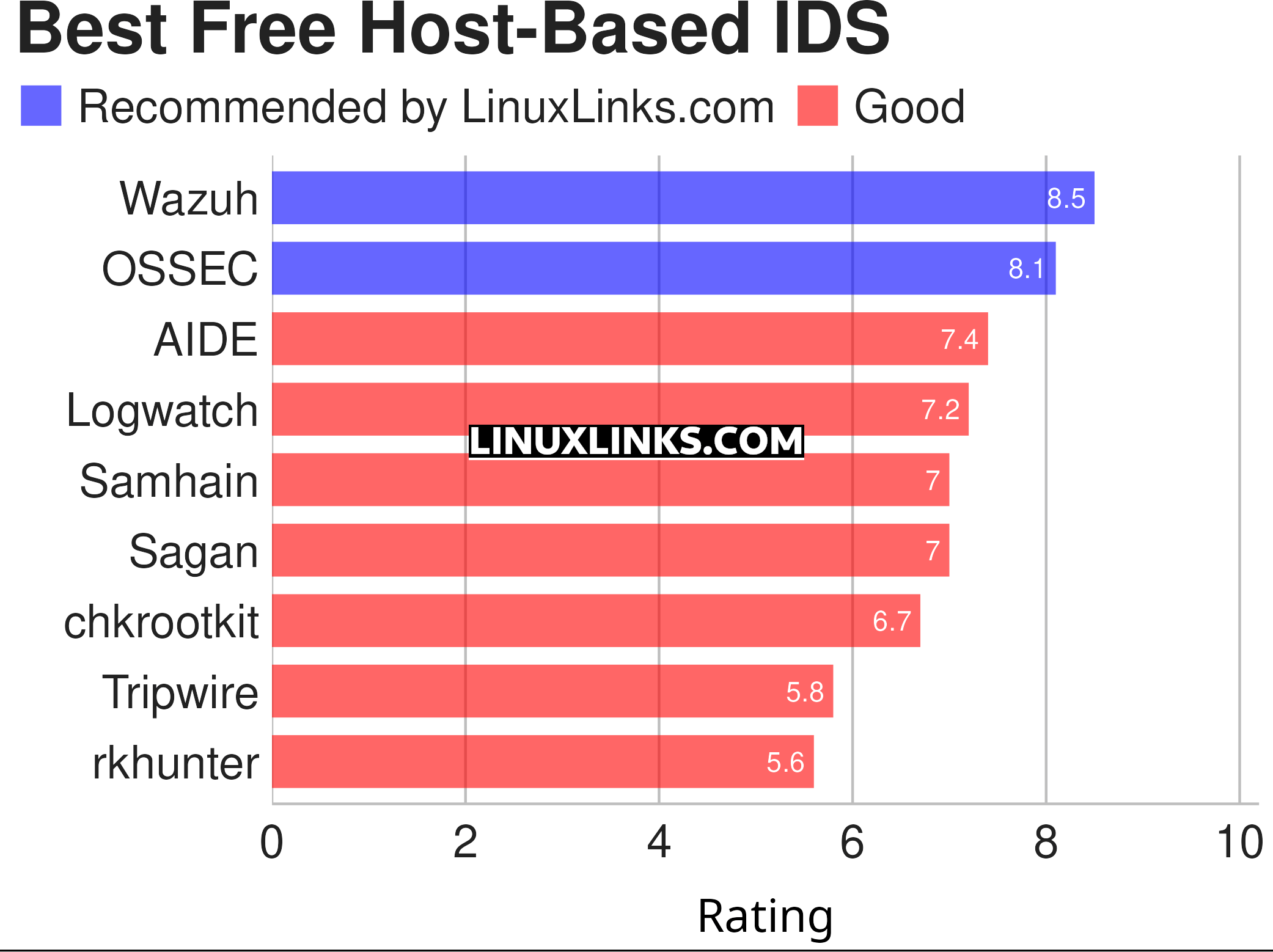
Here’s our verdict on the finest HIDS. We only feature open source software here.
Let’s explore the 9 HIDS. For each application we have compiled its own portal page, a full description with an in-depth analysis of its features, together with links to relevant resources.
| Host-Based Intrusion Detection Systems | |
|---|---|
| Wazuh | Platform used for threat prevention, detection, and response |
| OSSEC | Full platform to monitor and control your systems. |
| AIDE | Advanced Intrusion Detection Environment |
| Logwatch | Powerful and versatile log parser and analyzer |
| Samhain | File integrity checking and log file monitoring/analysis and more |
| Sagan | Multi-threads, high performance log analysis engine |
| chkrootkit | Locally checks for signs of a rootkit |
| Tripwire | Security and data integrity tool |
| rkhunter | Scans for rootkits, backdoors and possible local exploits |
This article has been revamped in line with our recent announcement.
If you’re looking for software-based NIDS, we recommend the best free and open source solutions in this separate article. NIDS can protect hundreds of computer systems from one network location. This helps make them a cost effective solution and easier to deploy than a HID.
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |
While Samhain is difficult to install, it’s technically superior to Tripwire OSS, AIDE, and OSSEC. (Tripwire went closed source.) Fail2ban is NOT a HIDS solution, it’s an application firewall. If you’re exposing ssh and internal network infrastructure to the outside world, then you have bigger security attack surface problems that cannot be solved by rate-limiting ssh.
Fail2ban is best described as intrusion prevention software. While technically not a HIDS, I don’t have a problem with it being covered here. Both monitor a network for malicious activity and/or policy violations.